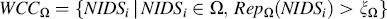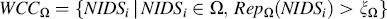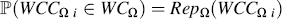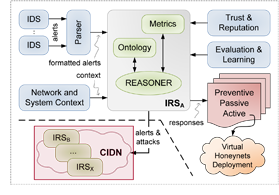
The design of a Collaborative Intrusion Detection Network (CIDN) has been defined in RECLAMO with the intention of building and sharing a collective knowledge about isolated alarms to efficiently and accurately detect distributed attacks. It is structured in a modular way to provide scalability, robustness, and real-time performance by clustering the closest autonomous Intrusion Detection Systems (IDS) in groups. The inward IDSs share and combine their collective knowledge (mainly alerts) of each other inside the same administrative domain, whereas a small group of them, each being the leader of its security domain, shares high-level information among the administrative domains involved in the collaborative detection process.
All alerts generated and shared by individual IDSs, either in a local or a high-level context, are previously assessed by a Wise Committee (WC) before being shared with the rest of the internal IDSs (intra-domain knowledge) or with other administrative domains (inter-domain knowledge). Following this procedure, both the IDSs and the administrative domains cannot publish or share their alerts without the prior consent of its WC, thereby avoiding the spread of alerts generated by malicious or compromised IDSs. More information about the concept of Collaborative Intrusion Detection Network (CIDN) and how it is structured can be found by clicking on
here and
here, whereas the corresponding software to define the design of several CIDNs in a testbed scenario can be found in the
Trust and Reputation module.
The election procedure of which NIDSs will be part of the Wise Committee is further explained below.
The Wise Committee (WC) is composed by some of the most trustworthy NIDSs belonging to the CIDN. More formally, the set of candidate NIDSs for becoming members of the WC of domain Ω is:
where ξΩ is a threshold determining the minimum level of reputation needed for an NIDS of domain Ω in order to become a member of its WC. Furthermore, each domain might decide the minimum and maximum number of members of its WC. Hence, if |WCCΩ| is in the range [minΩ, maxΩ] then all the candidates constitute automatically the WCΩ.
However, if |WCCΩ| > maxΩ then the probability of a candidate becoming a real member is equal to its global reputation within the domain:
Finally, if |WCCΩ| < minΩ, then ξΩ may be reduced until the minimum number of candidates is reached. It is also noteworthy that, applying the WC membership selection procedure described above, the results indeed are difficult for a malicious NIDS to become a member of its WC.
software download
You can download from the below link the source code to check the Wise Committee election described earlier. Note that this Java class code requires the ones developed in the
Trust and Reputation module for subsequent compilation and execution of this test.
Please don't hesitate to
contact us for any enquiries you might have.